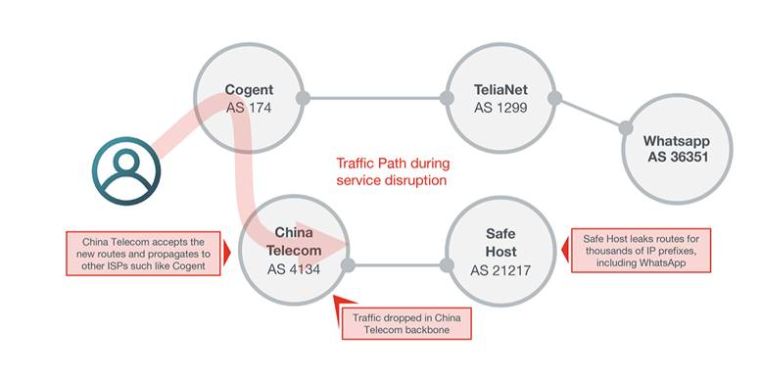
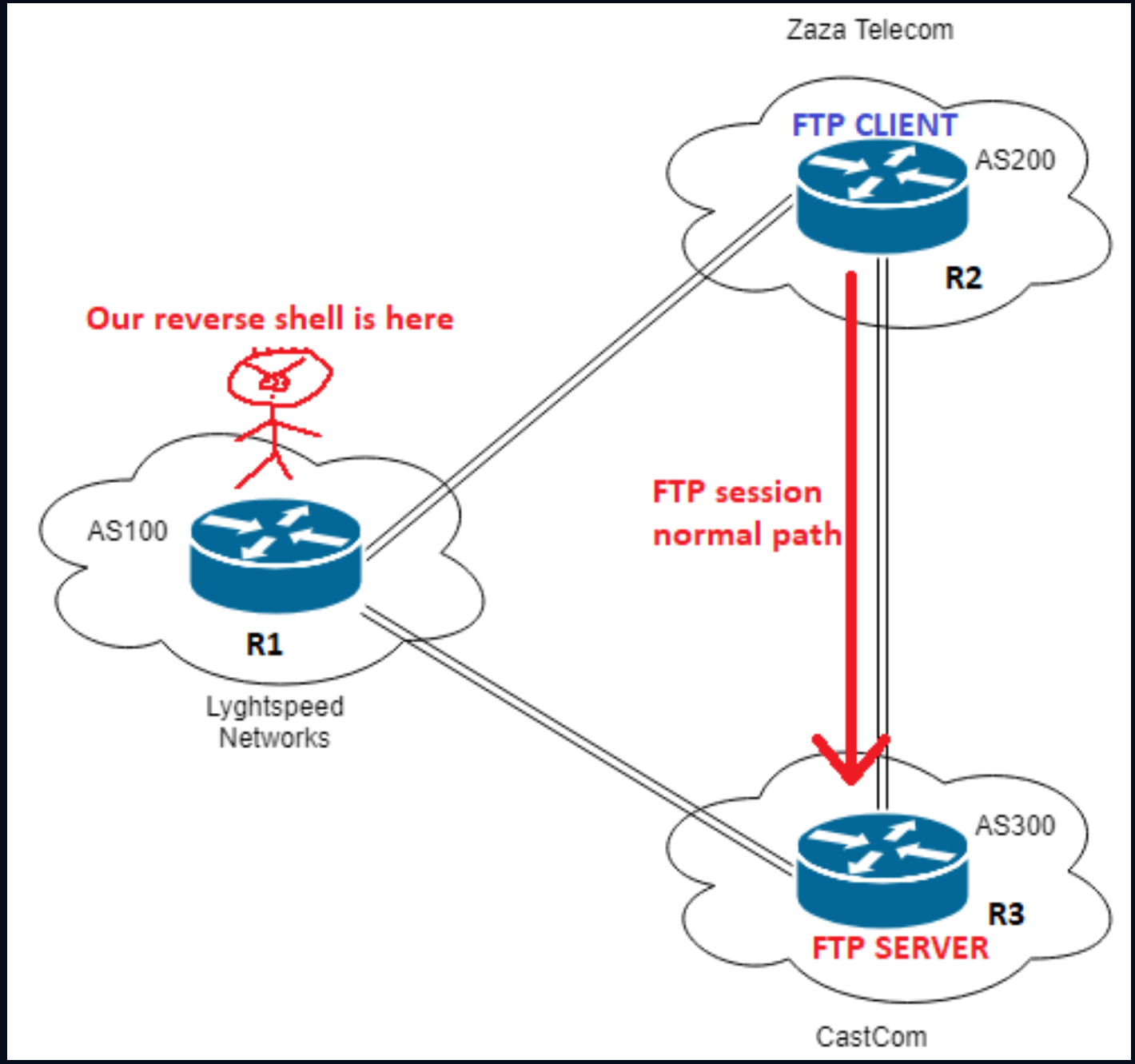
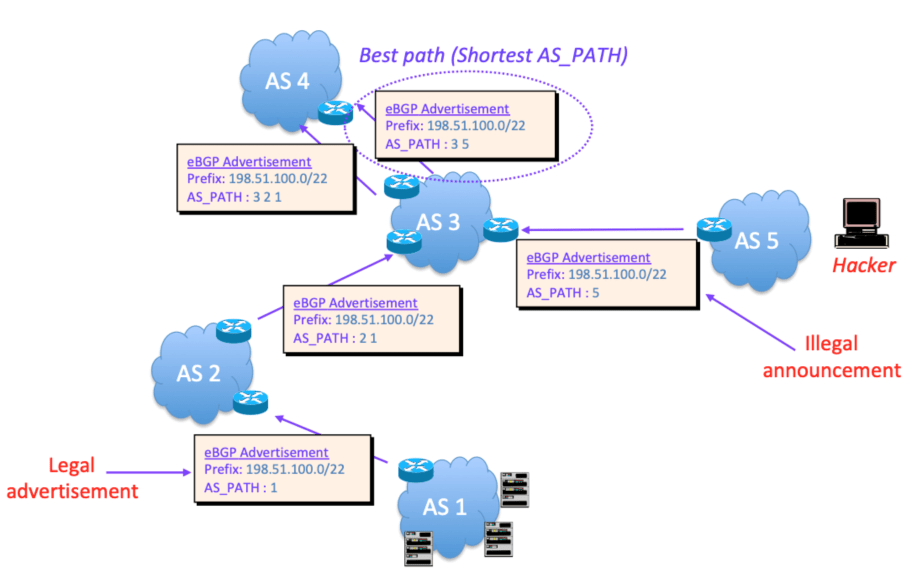
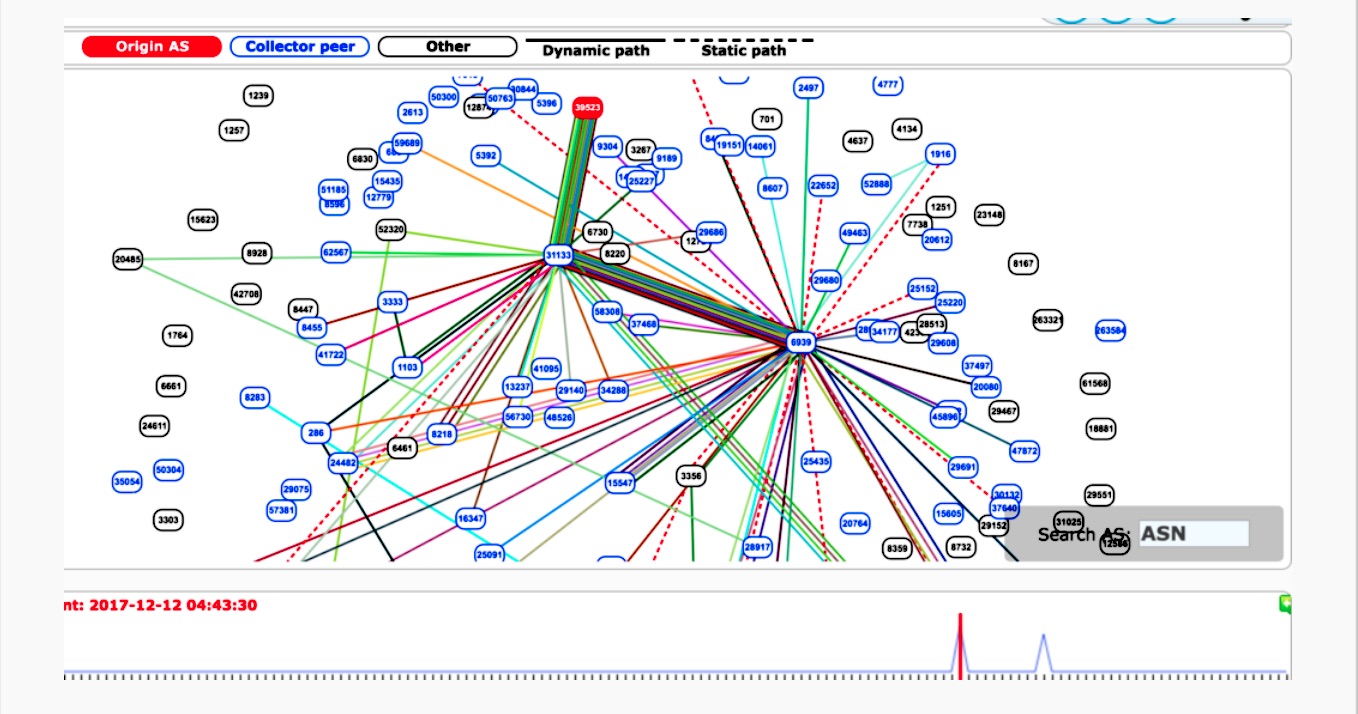
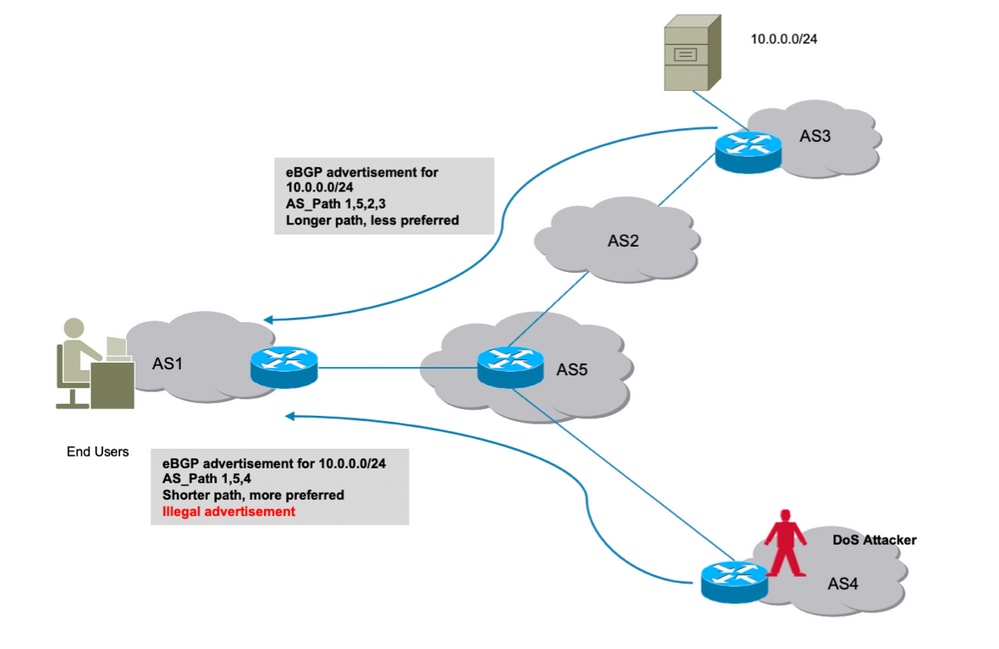
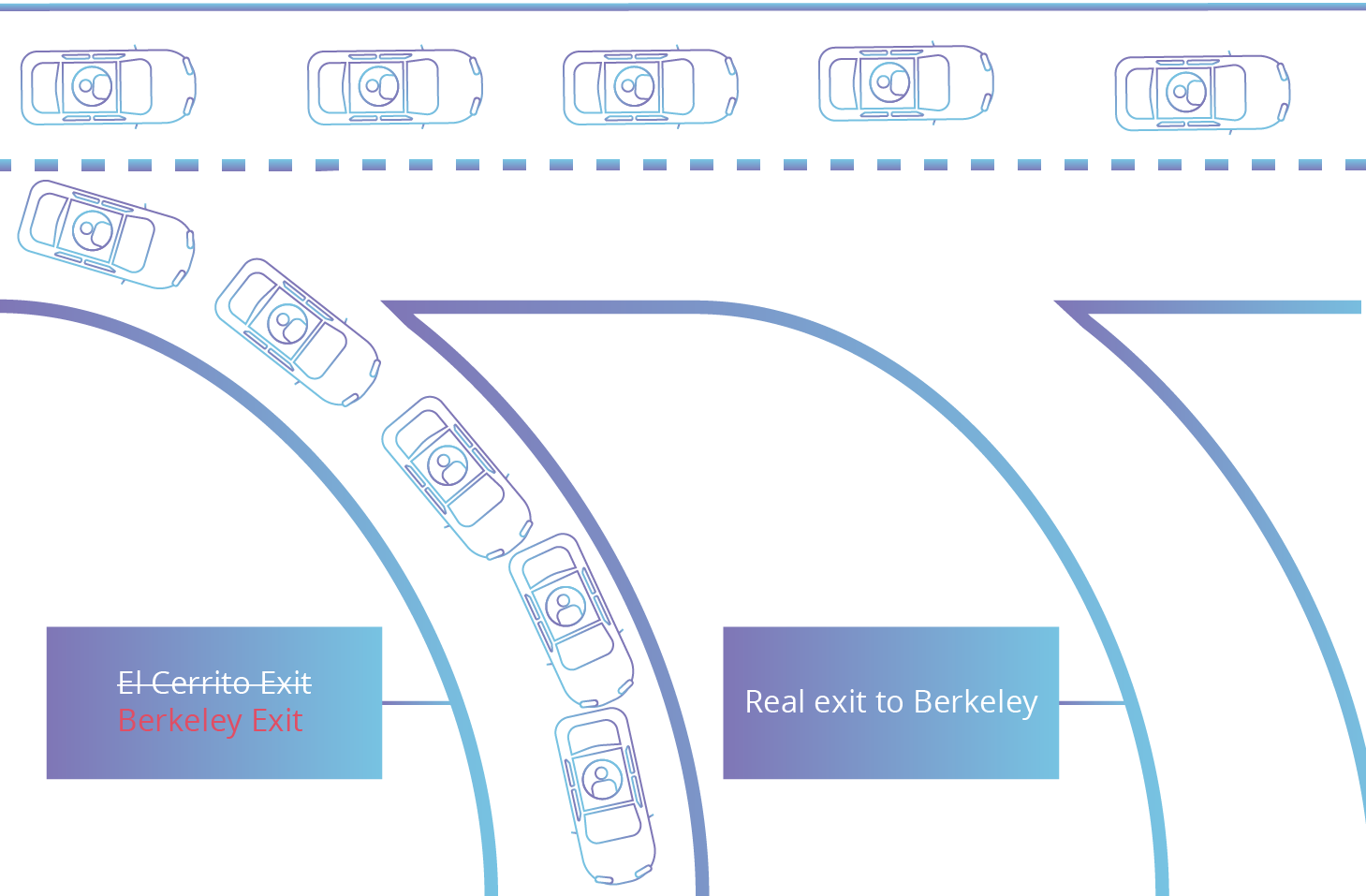
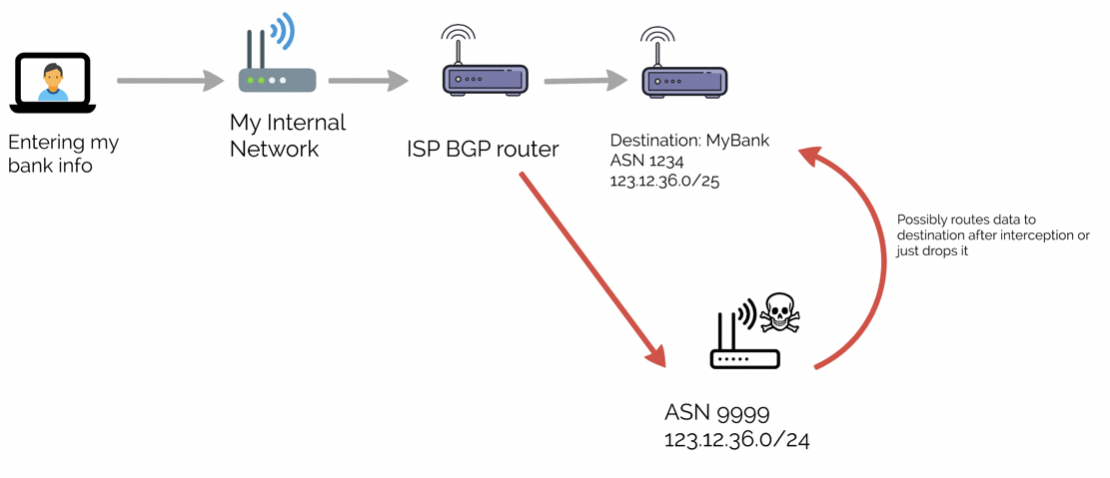
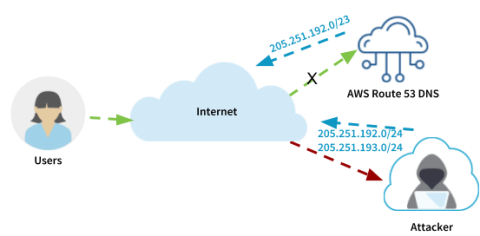
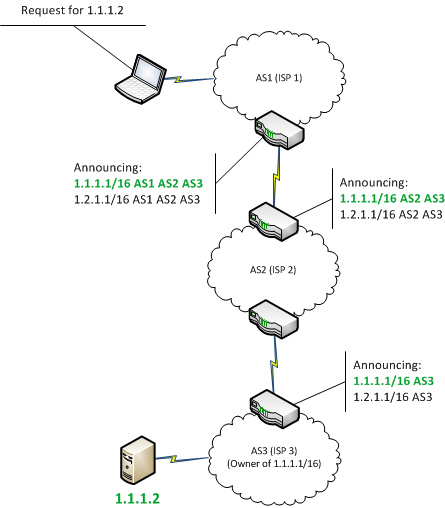
Sub-prefix hijacking 4) Sub-prefix and its AS Hijack: In this scenario,... | Download Scientific Diagram

BGP Hijackings Come Back! - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.