
Program: Computer Information Systems (Certificate of Completion), Cyber Security - Central New Mexico Community College - Acalog ACMS™

Center for Internet Security Computer security The CIS Critical Security Controls for Effective Cyber Defense Microsoft Benchmark, microsoft, blue, text png | PNGEgg







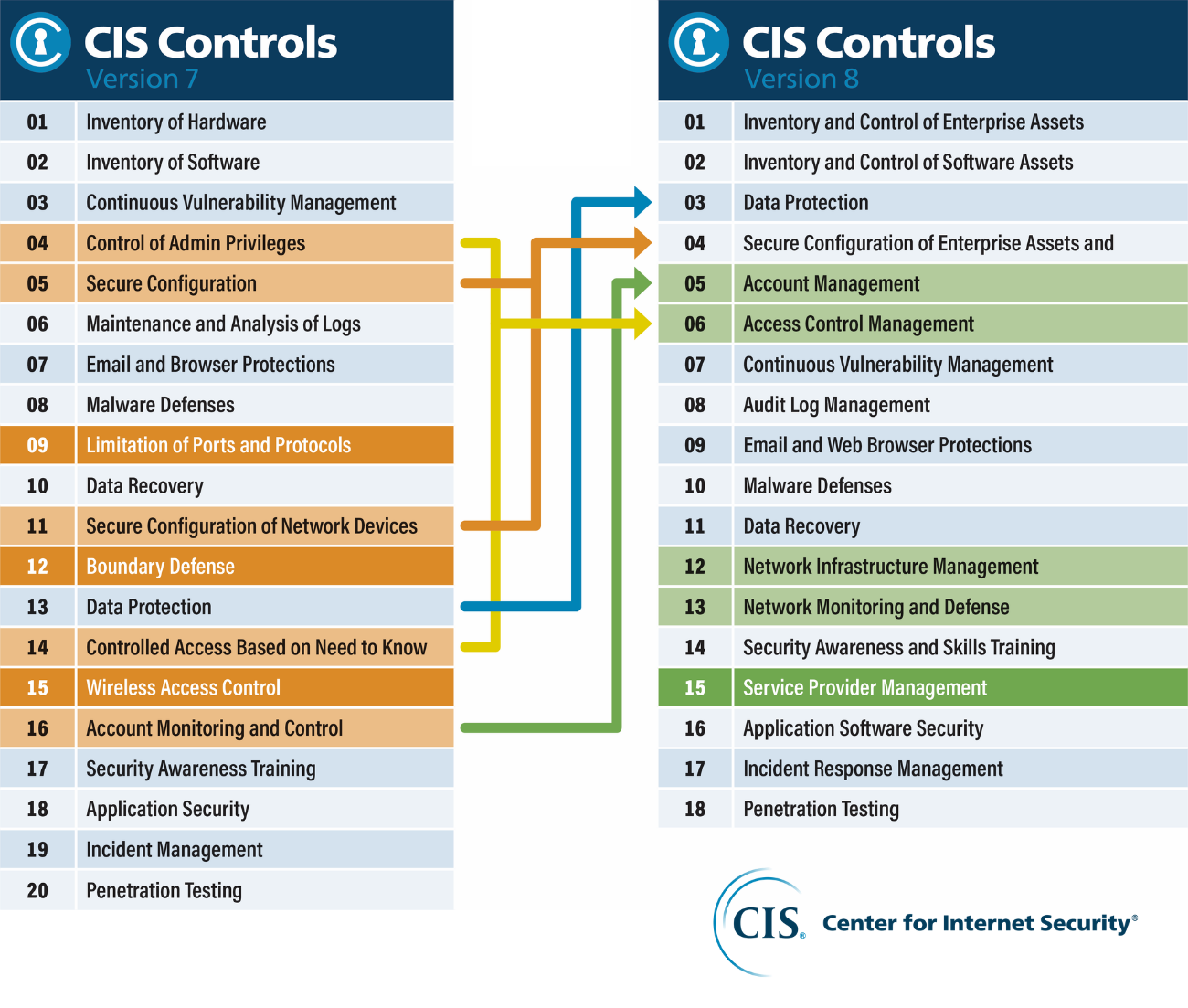



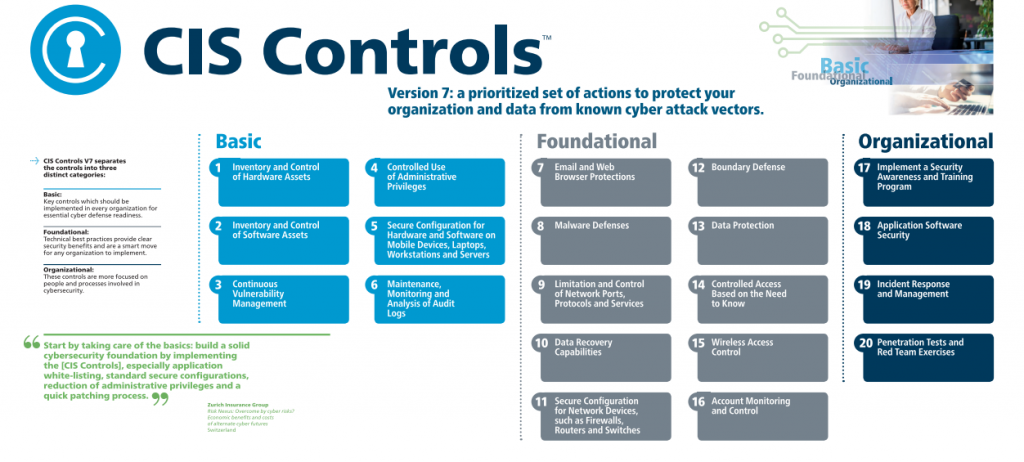




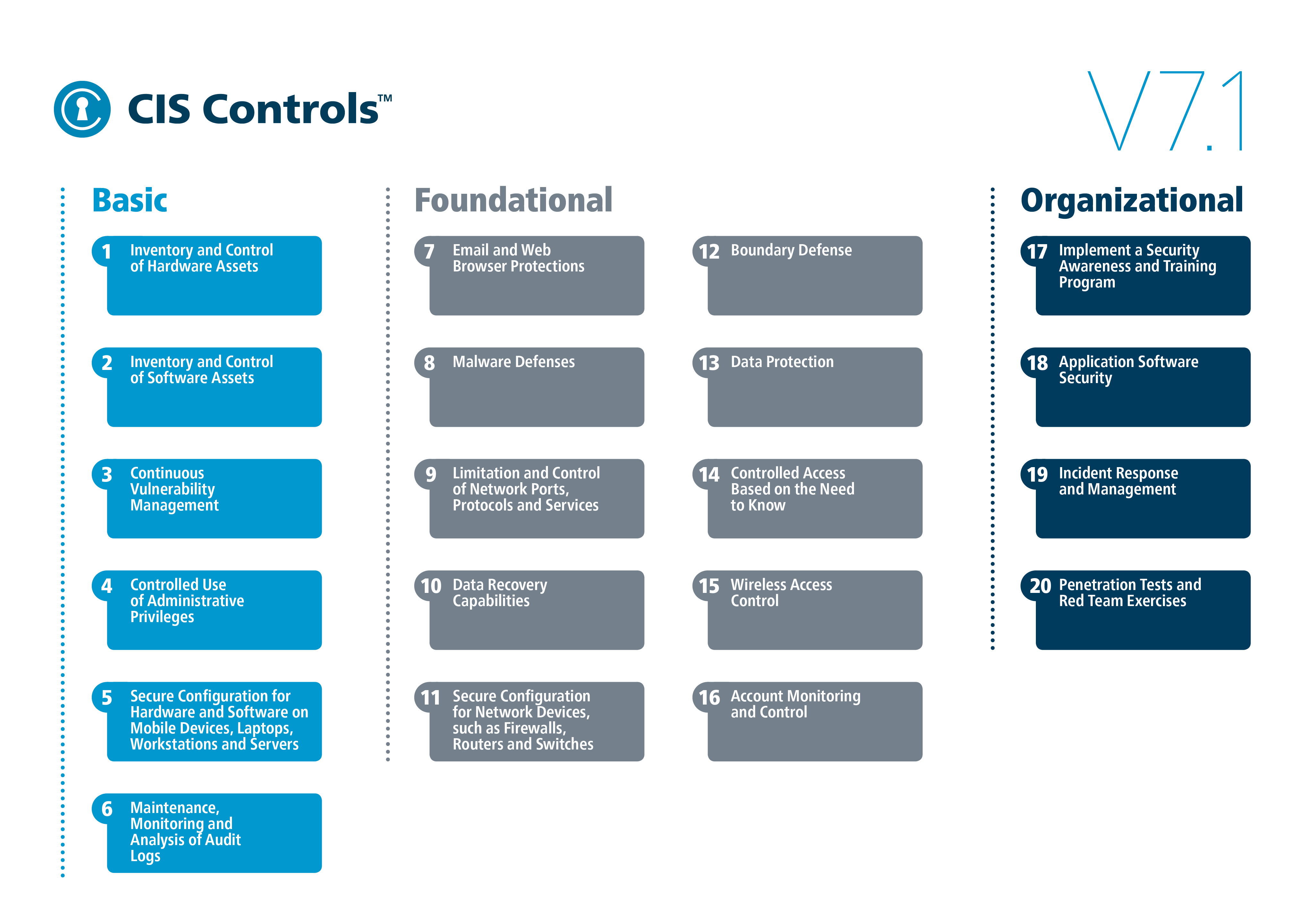



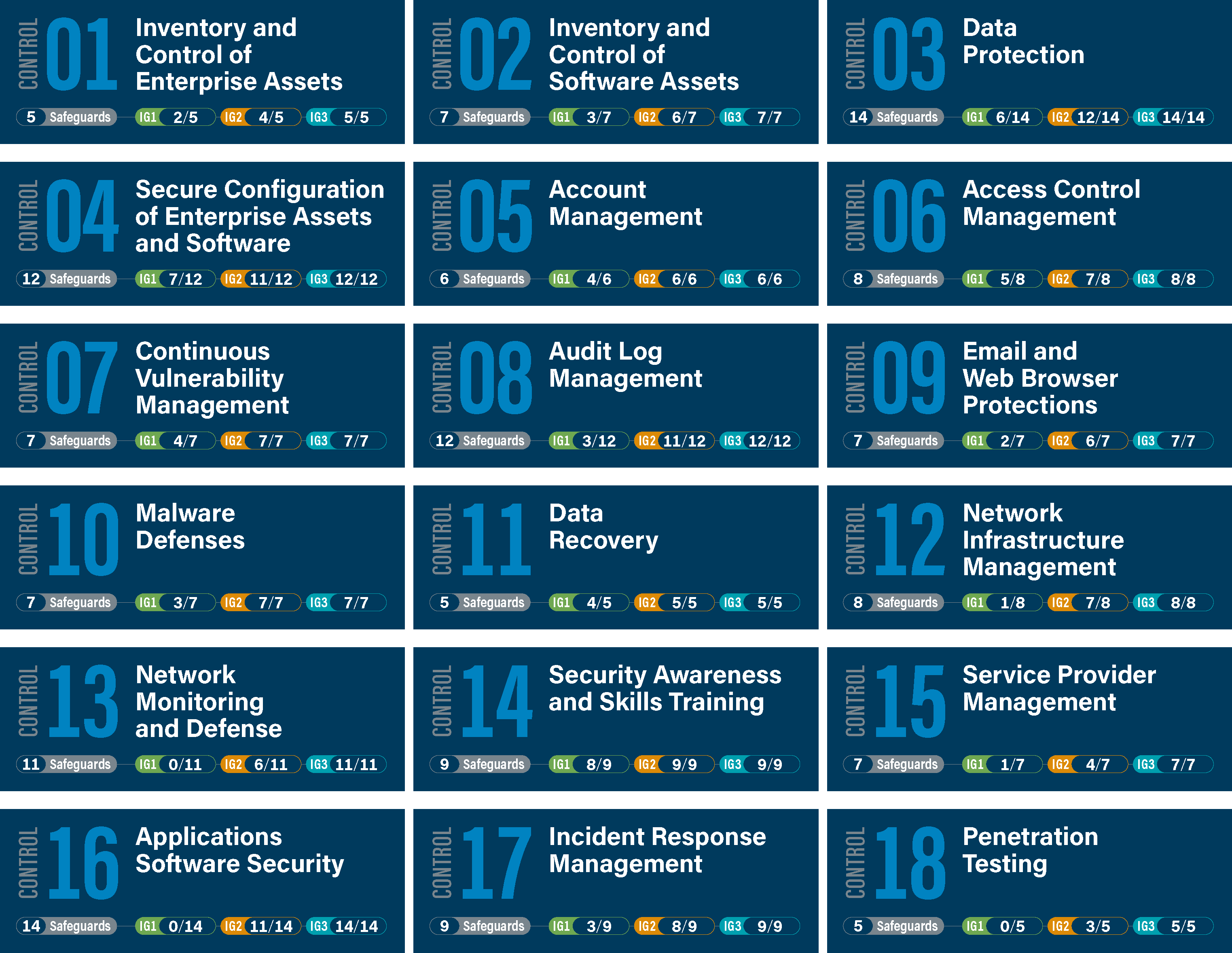

![INFOGRAPHIC] The 5 Ws for Building a Strong Cybersecurity Plan INFOGRAPHIC] The 5 Ws for Building a Strong Cybersecurity Plan](https://www.cisecurity.org/-/media/project/cisecurity/cisecurity/data/media/img/uploads/2021/09/blog-5-ws-cybersecurity-v21092.png?rev=5e7a6e5477cb42a194da08cda40bb33a&hash=F85C3C60CCC91A02A8CC4C43755841E5)