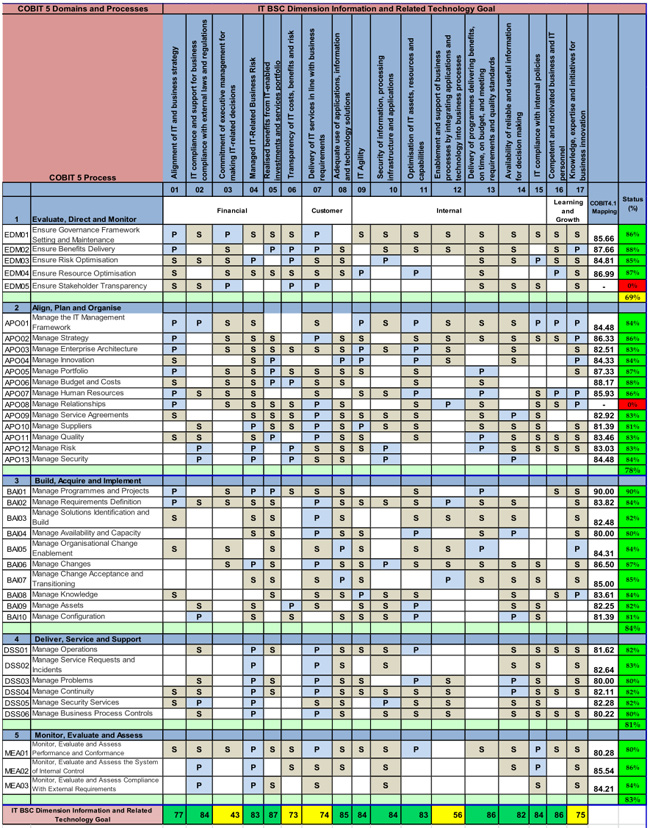
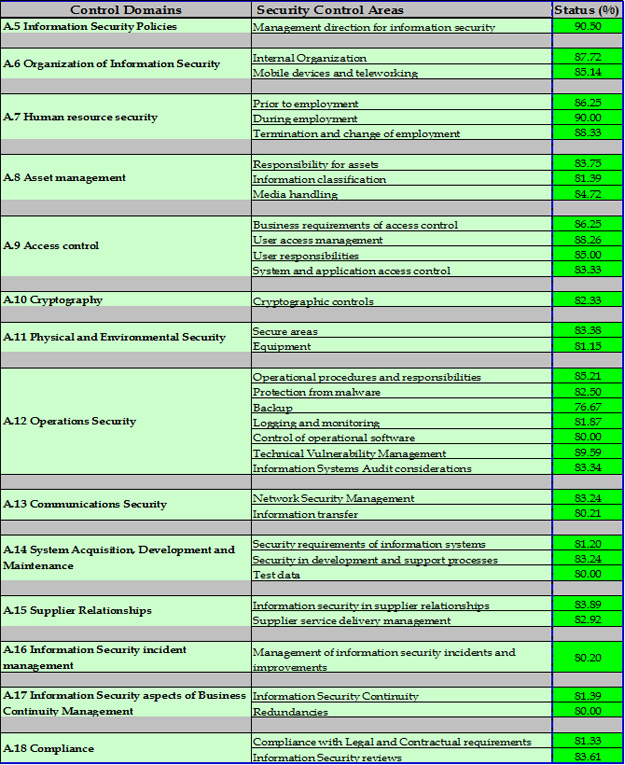
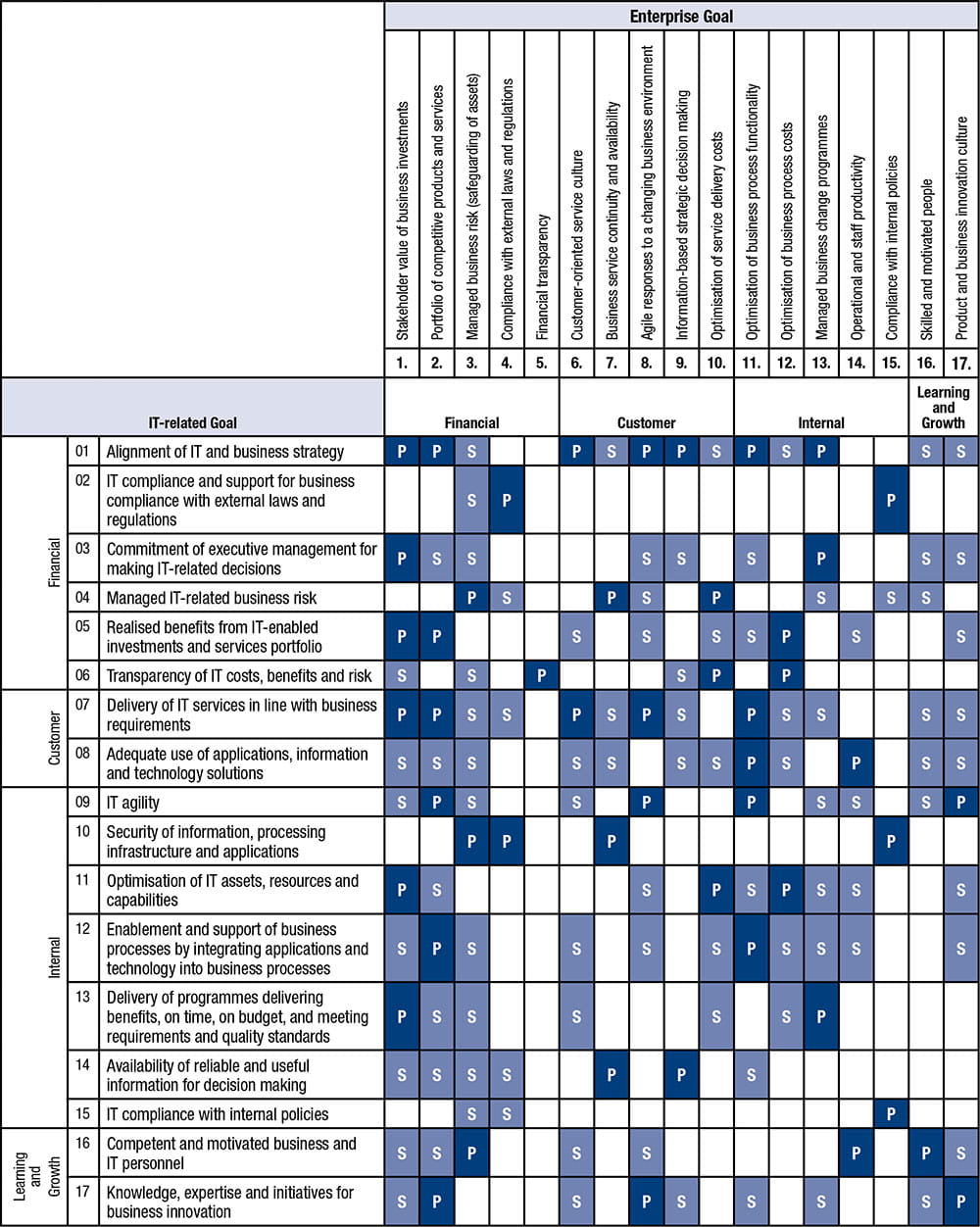
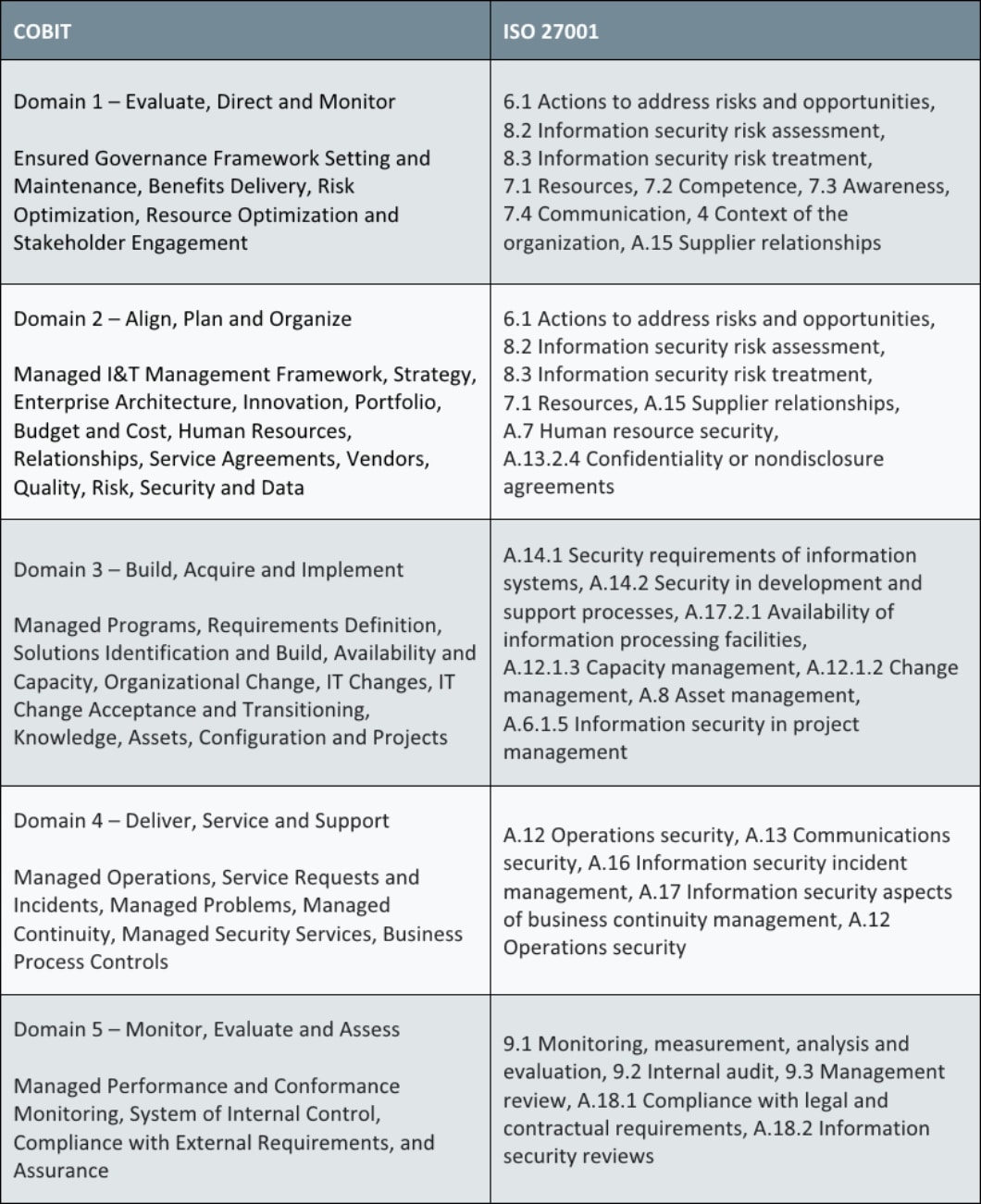
![PDF] An Approach to Map COBIT Processes to ISO/IEC 27001 Information Security Management Controls | Semantic Scholar PDF] An Approach to Map COBIT Processes to ISO/IEC 27001 Information Security Management Controls | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/4d69c7653470b94e6a0818f92eb9e706e82b5608/10-Table2-1.png)
PDF] An Approach to Map COBIT Processes to ISO/IEC 27001 Information Security Management Controls | Semantic Scholar
![PDF] An Approach to Map COBIT Processes to ISO/IEC 27001 Information Security Management Controls | Semantic Scholar PDF] An Approach to Map COBIT Processes to ISO/IEC 27001 Information Security Management Controls | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/4d69c7653470b94e6a0818f92eb9e706e82b5608/5-Figure1-1.png)
PDF] An Approach to Map COBIT Processes to ISO/IEC 27001 Information Security Management Controls | Semantic Scholar

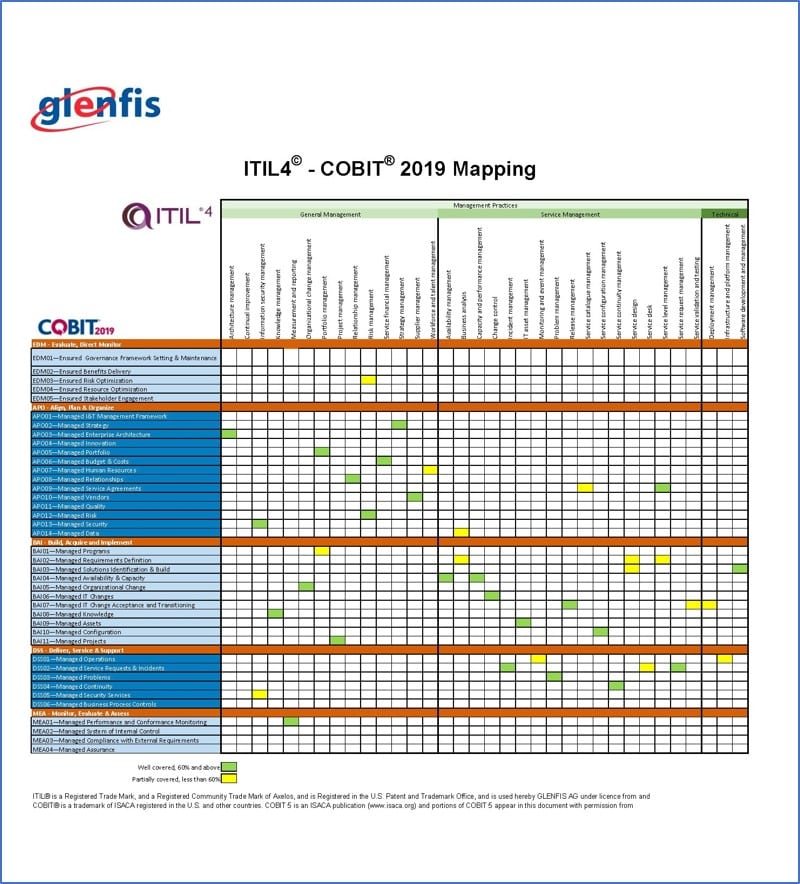
Combining ITIL, COBIT and ISO/IEC 27002 in Order to Design a Comprehensive IT Framework in Organizations | Semantic Scholar

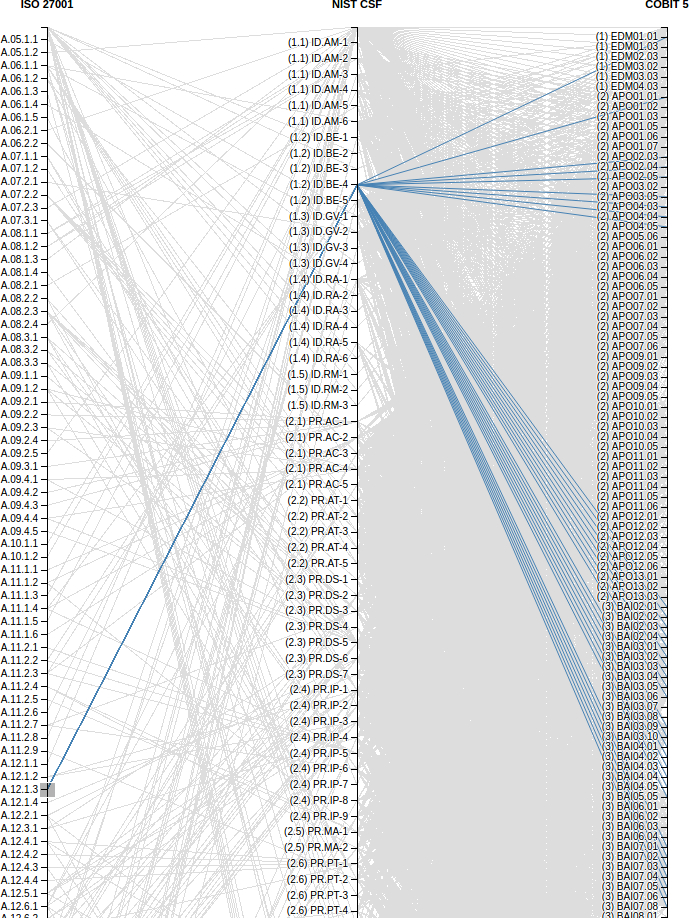
PDF) An Approach to Map COBIT Processes to ISO/IEC 27001 Information Security Management Controls | Razieh Sheikhpour - Academia.edu
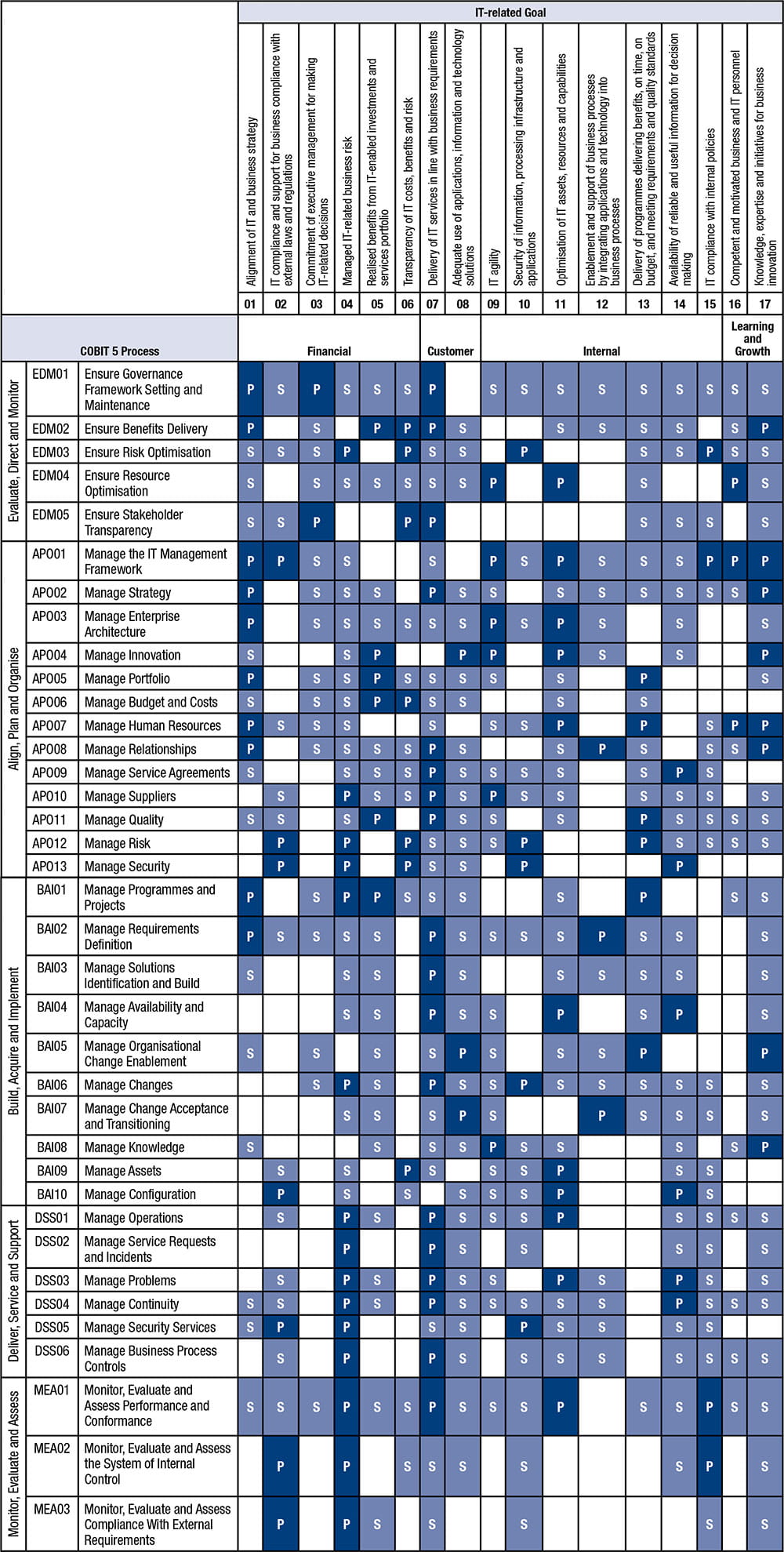
Mapping and Integration of Enterprise Governance of IT Practices Information Systems and Computer Engineering
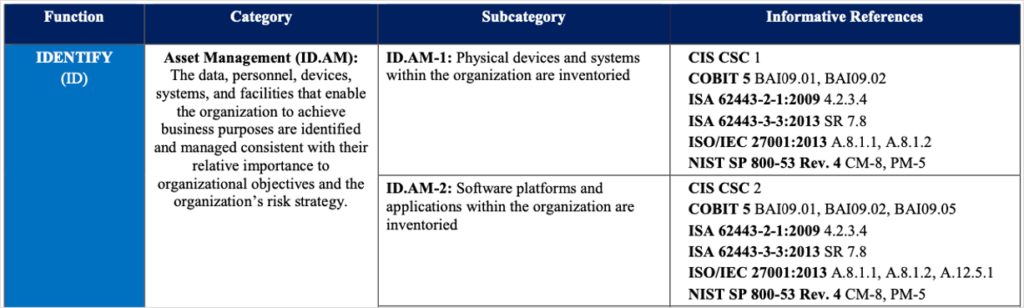




![PDCA Model Applied to ISMS Processes and ISO/IEC 27001 Mapping [2] | Download Scientific Diagram PDCA Model Applied to ISMS Processes and ISO/IEC 27001 Mapping [2] | Download Scientific Diagram](https://www.researchgate.net/profile/Diogo-Proenca/publication/325786419/figure/tbl2/AS:692194507780096@1542043439006/ISMS-Maturity-Model_Q320.jpg)