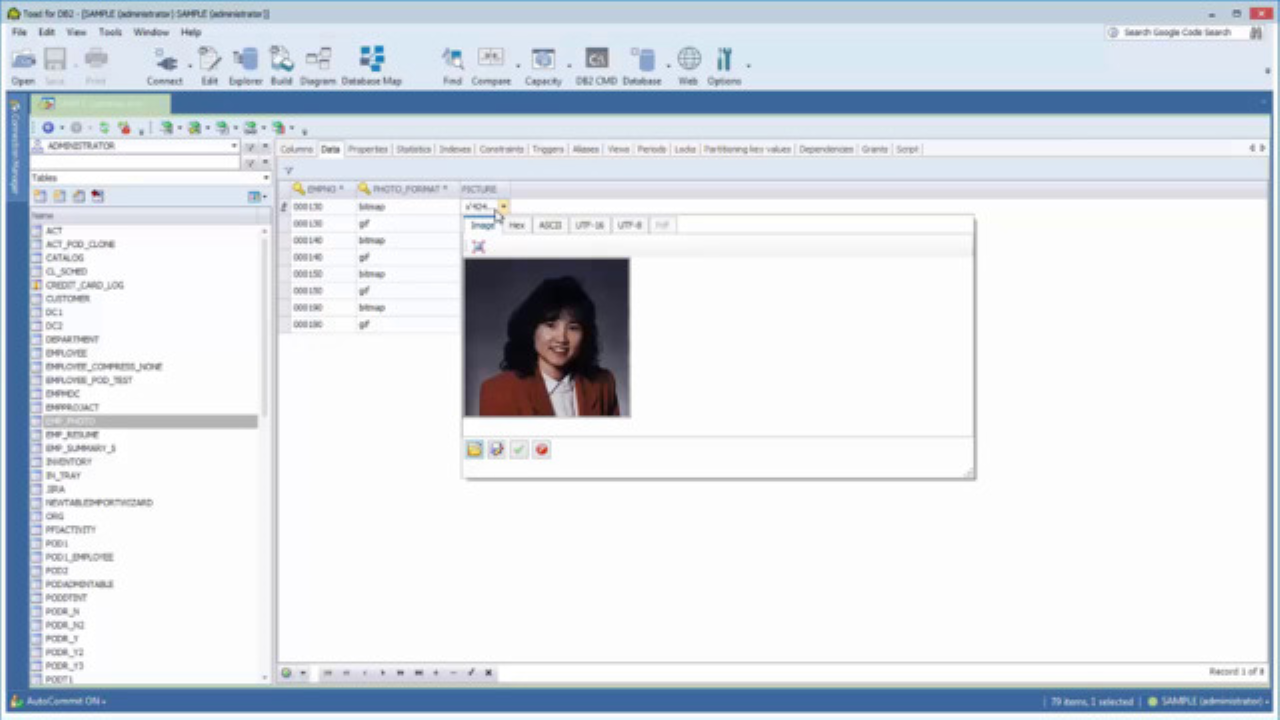
Amazon.com: Ciberseguridad: Guía completa para principiantes aprende todo de la ciberseguridad de la Aa la Z(Libro En Español/Spanish version) (Spanish Edition) eBook : Lewis, Elijah : Kindle Store

Amazon.com: Ciberseguridad: Guía completa para principiantes aprende todo de la ciberseguridad de la Aa la Z(Libro En Español/Spanish version) (Spanish Edition) eBook : Lewis, Elijah : Kindle Store

La ciberseguridad y la digitalización encabezan la lista de riesgos para las empresas europeas | Seguridad | IT User
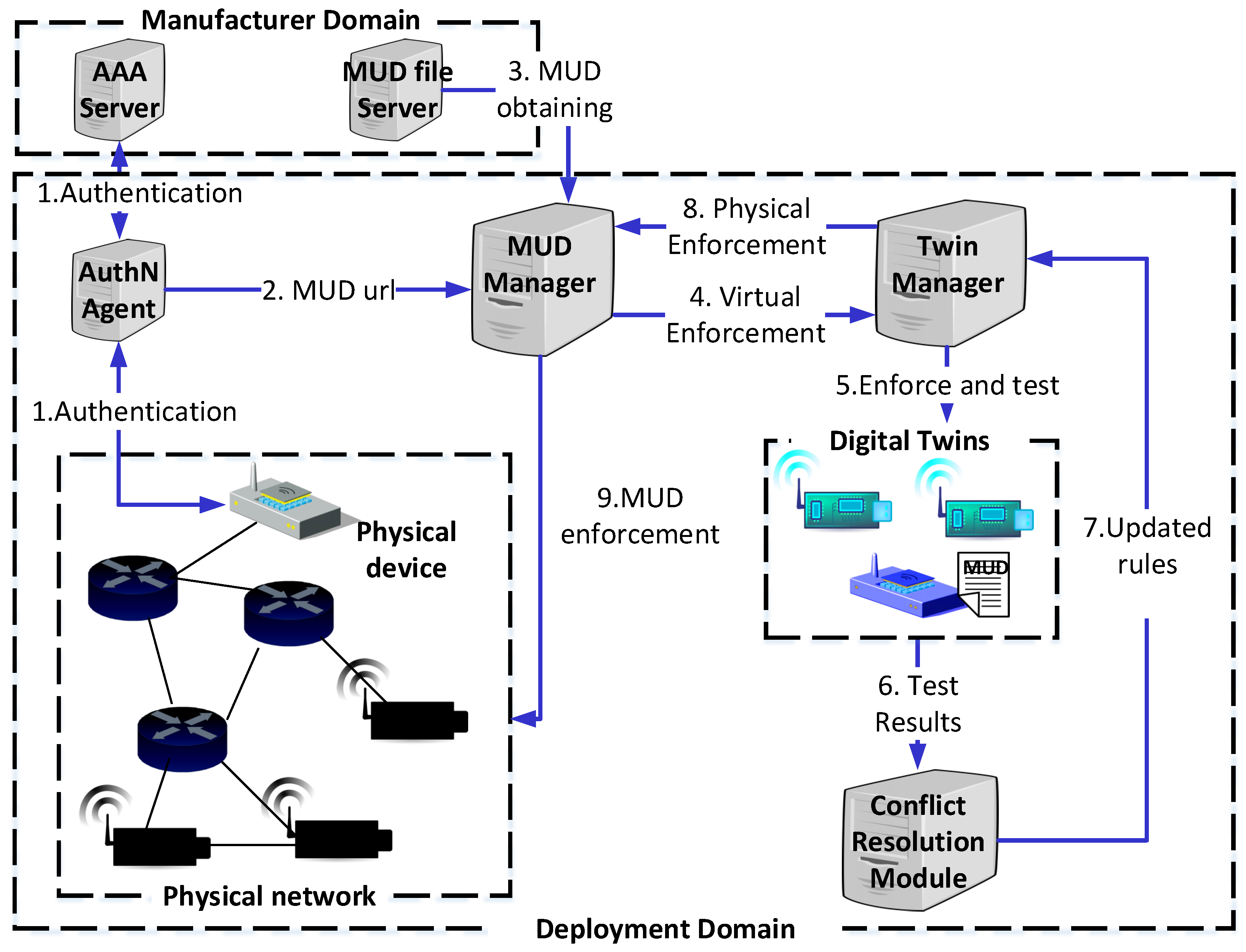
Applied Sciences | Free Full-Text | Enforcing Behavioral Profiles through Software-Defined Networks in the Industrial Internet of Things | HTML



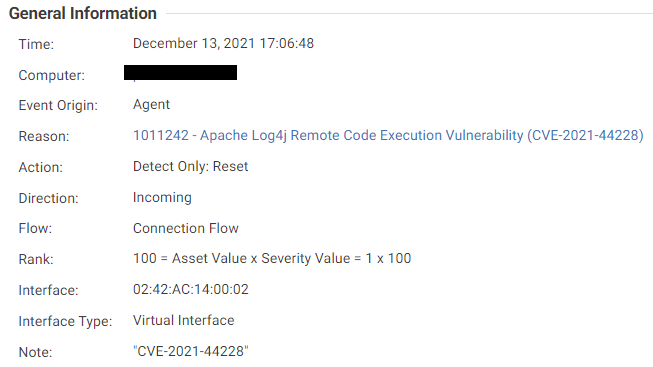



.png)