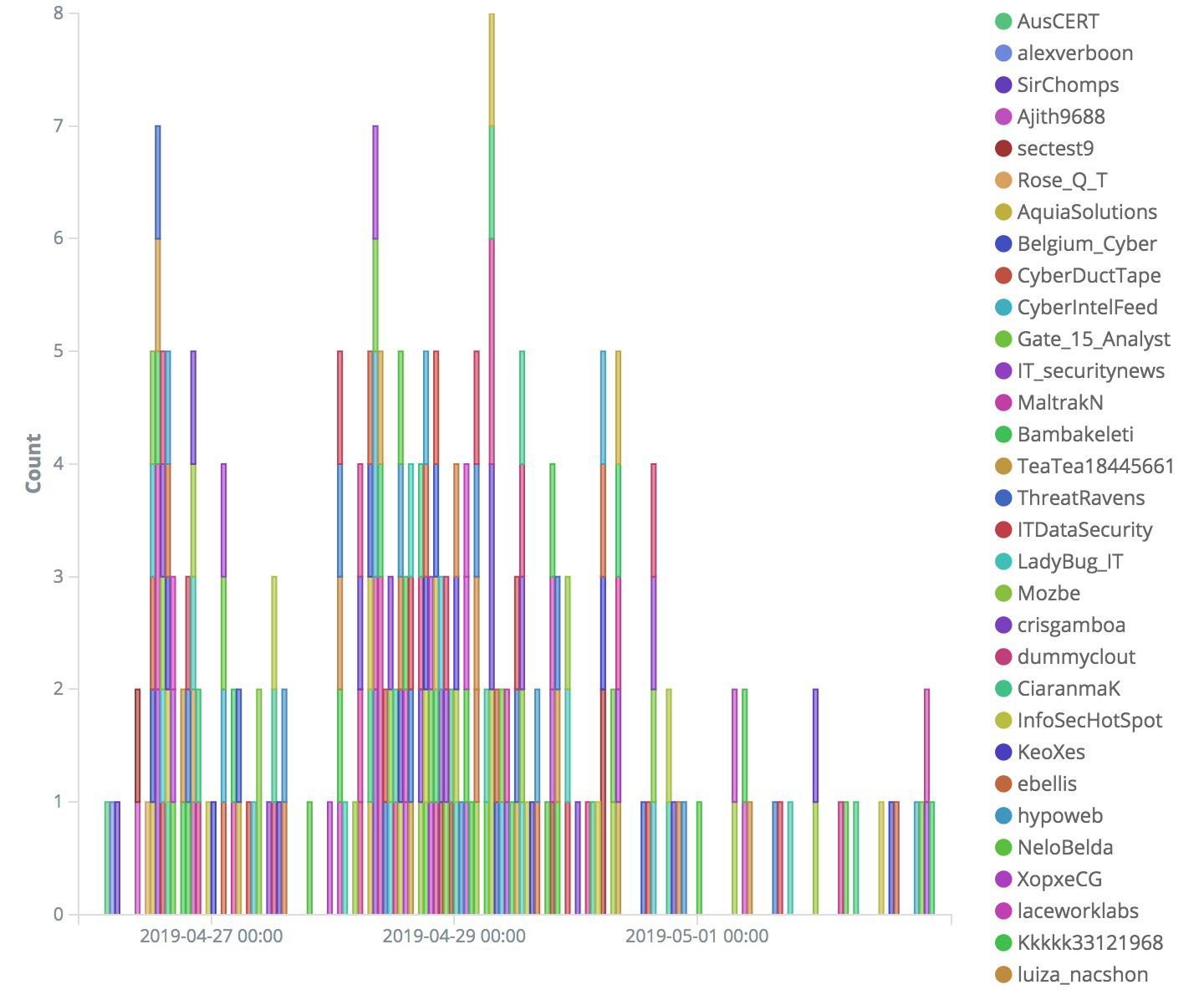
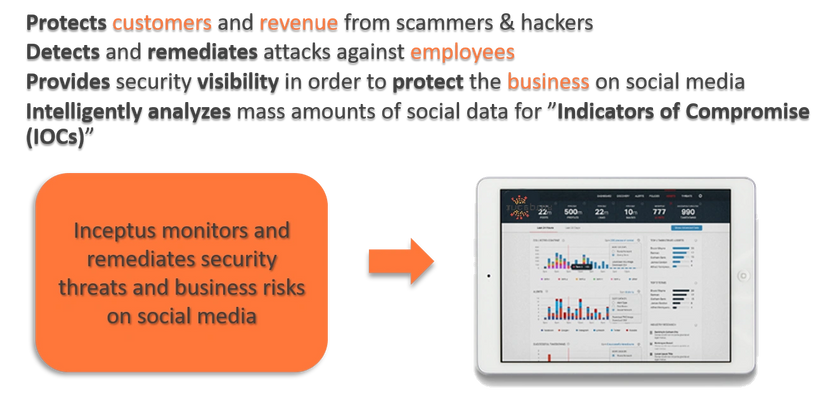
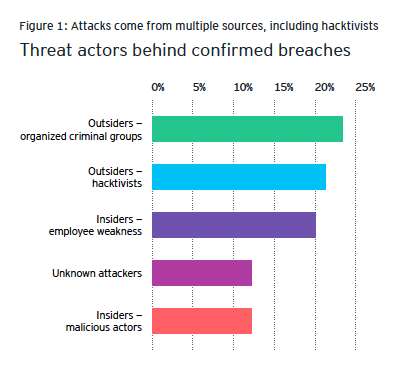
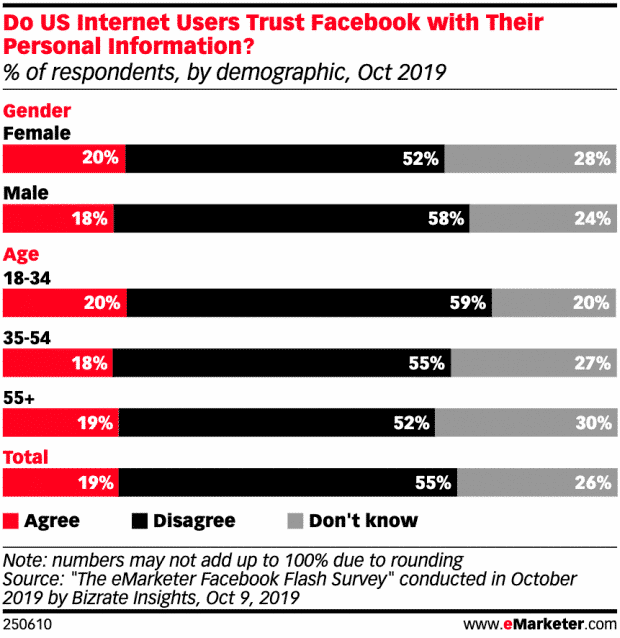
Hunting Threats on Twitter: How Social Media can be Used to Gather Actionable Threat Intelligence - Informazioni sulla sicurezza

Hunting Threats on Twitter: How Social Media can be Used to Gather Actionable Threat Intelligence - Informazioni sulla sicurezza
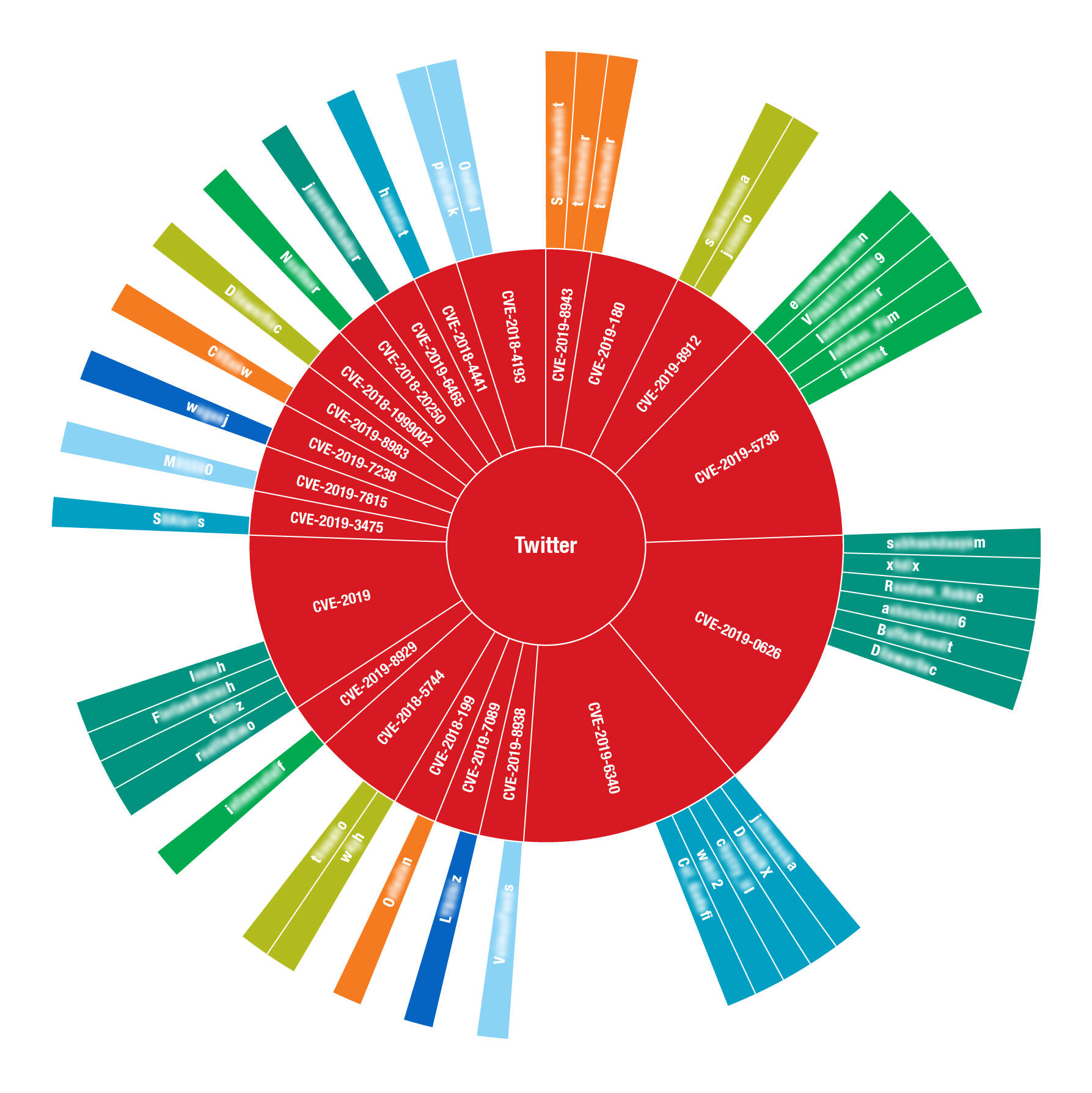
Hunting Threats on Twitter: How Social Media can be Used to Gather Actionable Threat Intelligence - Informazioni sulla sicurezza